Claroty Continuous Threat Detection
Essential Security Monitoring With Real-Time IoT-OT Visibility
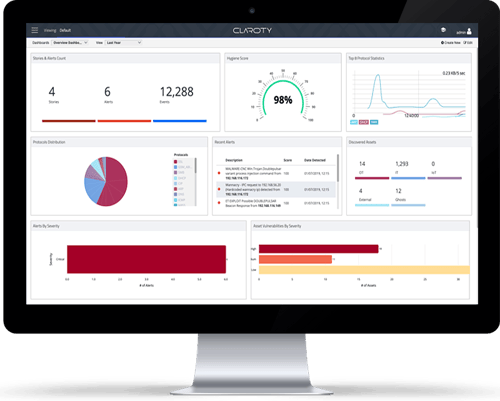
CTD was specifically designed to ensure safe, secure and reliable operations in large, complex networks – ensuring zero impact to the operational processes and underlying devices.
By extracting fine-grained details about each device on the industrial network, profiling all communications and protocols, CTD generates a behavioural pattern that characterises legitimate traffic, alerting upon any network changes, vulnerabilities and threats.
Identify zero-day and known threats with CTD’s five Deep Packet Inspection (DPI) detection engines.
Identify devices with known vulnerabilities for fast and efficient mitigation.
Automatically discover and manage IoT and OT devices with a centralised, user-friendly interface.
Consolidate and centrally manage data from multiple disparate sites.
AI-Powered Noise Elimination
ML Alert Algorithm: Correlate past and predictive models of behaviour with online patterns to eliminate distracting and costly noise in the form of false positives and normal changes.
Fast Time-to-Value
The industry’s first real application of AI for OT and IoT that correlates real-time changes with online patterns and network behaviours to create detailed profiles for every device according to the process state to quickly detect critical conditions.
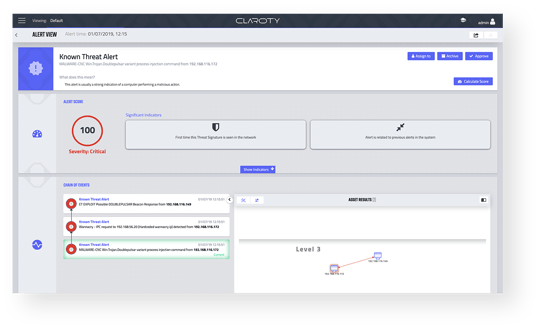
Eliminate Alert Noise
Leveraging AI-powered dynamic learning algorithms.
Prioritise Risk-Based Indicators
Facilitate Risk Triage and Root Cause Analysis (RCA) with visibility into the chain of events leading up to every alert.
Accommodate Varying Risk Appetites
Speed workflows leveraging customisable alerting thresholds.
Accelerate Digital Transformation
Roll-out across multiple sites and reach full-scale enterprise deployment in less than 60 days and lower Total Cost of Ownership (TCO).
Identify and accelerate asset detection with Claroty Edge, see how with this simple video
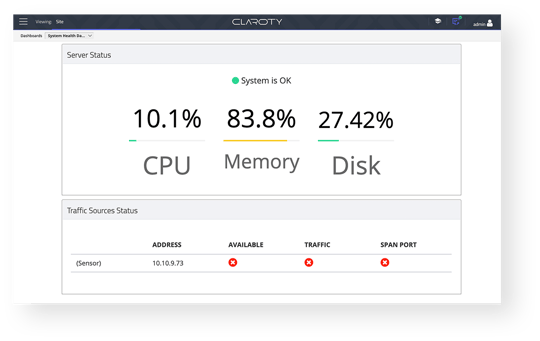
Deployment at Scale
Enterprise-wide scalability with optimum performance and stability.
Enterprise-Wide Visibility
Consolidated OT cyber-security and visibility across highly distributed sites.
Optimise TCO
Enterprise-wide deployment in less than 60 days leveraging highly adaptive, multiple appliance models and flexible deployment architectures.
Data Sheets
Copyright © 2024 All Rights Reserved by SolutionsPT.