Tenable One | Anticipate Attacks & Reduce Cyber Risks - by SolutionsPT
As a leader in your business and as a responsible organisation you want to meet the needs of your stakeholders and this requires you to manage your Operational Technology cyber security risk. To do this you want to engage with a supplier that can provide as many of your cyber needs as possible, that is a pleasure to work with and who will give you the knowledge you need to do your job well.
SolutionsPT’s philosophy for Cyber Security is that we will provide a service that best suits the needs of our customers so they can suitably reduce their risk and ensure compliance.

Threats have evolved. Get ahead of cyber risk
Your attack surface is growing, always changing and more interconnected than ever. With specialised security tools offering an incomplete picture, it can feel impossible to answer the question, “How secure are we?”
Tenable’s approach to exposure management combines visibility across all facets of the attack surface with business context so you can accurately understand your organisation’s cyber risk and prioritise mitigation.
GET A SINGLE, UNIFIED VIEW OF YOUR MODERN ATTACK SURFACE
Tenable One is an exposure management platform that combines risk-based vulnerability management, web application security, cloud security and identity security.
Tenable One helps your cybersecurity teams gain a unified view of all assets and associated software vulnerabilities, configuration vulnerabilities and entitlement vulnerabilities, whether on-prem or in the cloud, to understand where you are exposed to risk.
The platform helps security leaders anticipate the consequences of a cyber attack by drawing upon the industry’s largest data set and understanding relationships between assets, exposures, privileges and threats across an attack path.
Security executives and business leaders have a centralized and business-aligned view of cyber risk. Clear KPIs show progress over time with benchmarking against external peers. The platform provides actionable insights into your overall cyber risk, with the ability to drill into departmental or operational units.
Built on Nessus, the Gold Standard in Vulnerability Assessment
Understanding your vulnerabilities is foundational to exposure management, and Nessus is at the core of Tenable One. Trusted by tens of thousands organisations worldwide to assess their modern attack surfaces, Nessus provides an accurate picture to help you do your work quickly and effectively.
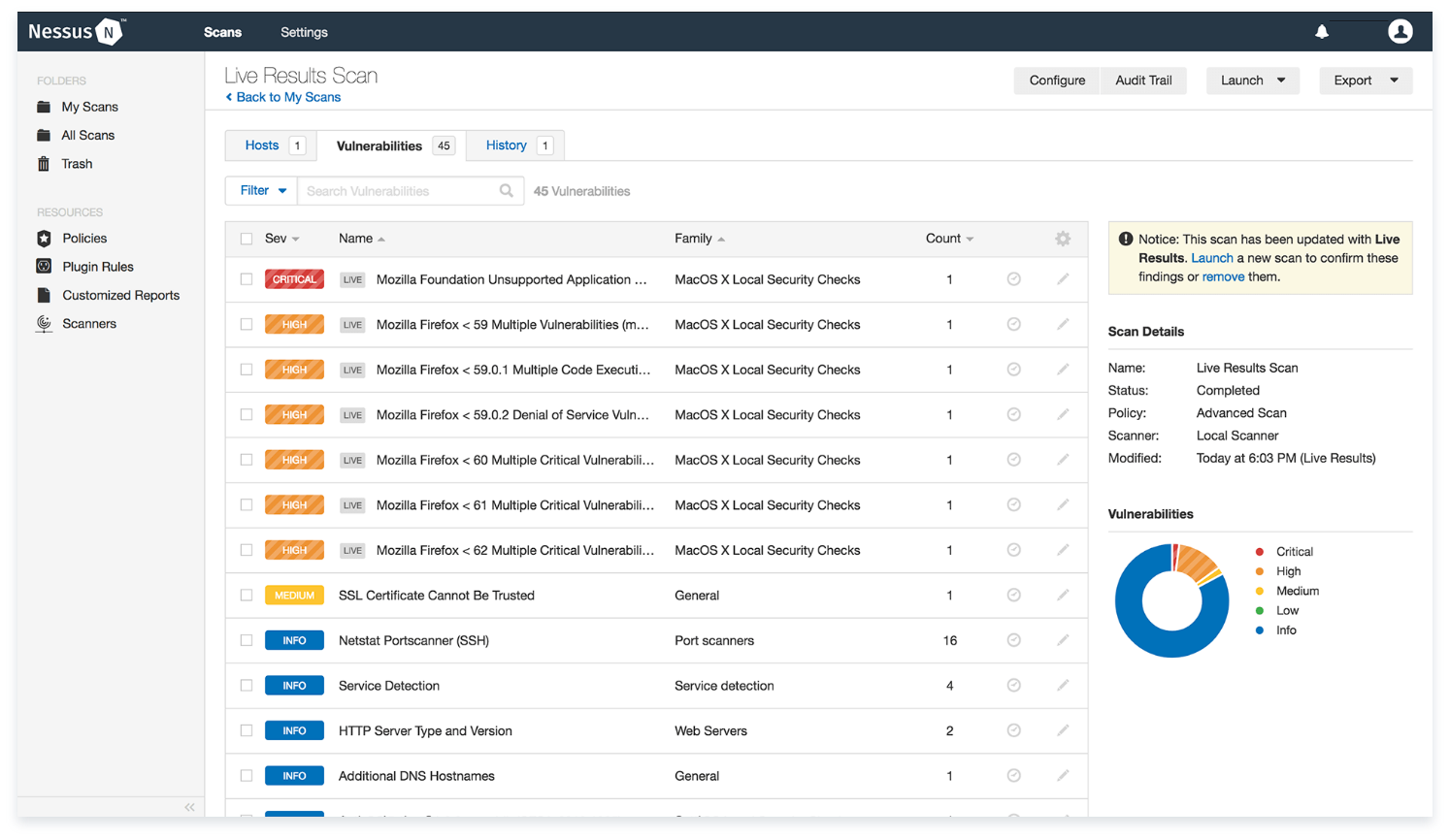
Quantify Your Exposure
Exposure View enables focused security efforts through clear, concise insight into your organization’s security exposure through a unified global exposure score drawn from a variety of different data sources.It helps answer such critical questions as:
- How secure are we?
- Where do we stand in our preventative and mitigation efforts?
- How are we doing over time?
- What are the key events?
See Everything, Eliminate Blind Spots
Comprehensive Asset Inventory provides full visibility into all assets and exposures regardless of data source (vulnerability management, web app security, cloud security and active directory security, etc.). This centralized view streamlines analysis, simplifies reporting and helps you take action faster.
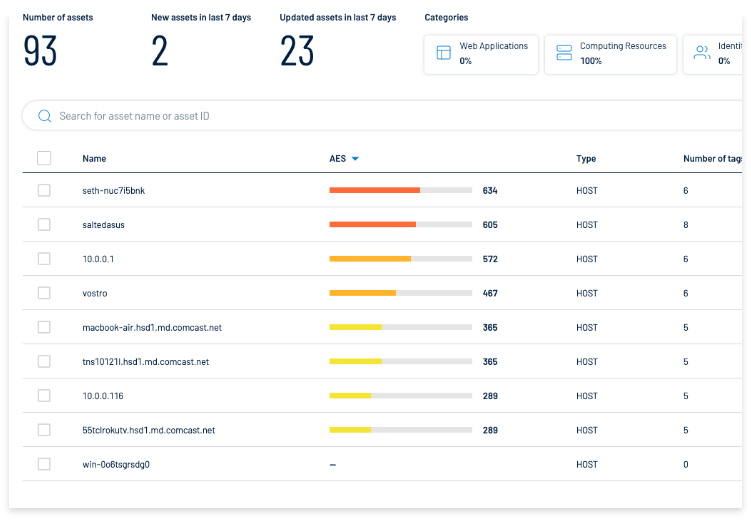
Make Comparisons
Compare cyber risk between business units or locations internally, and against industry peers externally, to determine where and when to make key human and financial investments.
01 Exposure Analytics
How secure is the business? Meet your Cyber Exposure Score
Calculate, communicate and compare your cyber exposure while managing risk with Tenable Lumin.
For the first time ever, you can visualize and explore your Cyber Exposure, track risk reduction over time, measure the effectiveness of your security operations and benchmark against your peers.
Use Tenable Lumin, an advanced visualization, decision support, analytics and measurement solution, to understand and reduce your Cyber Exposure. Lumin transforms vulnerability data into meaningful insights to help you manage cyber risk across your entire organization.
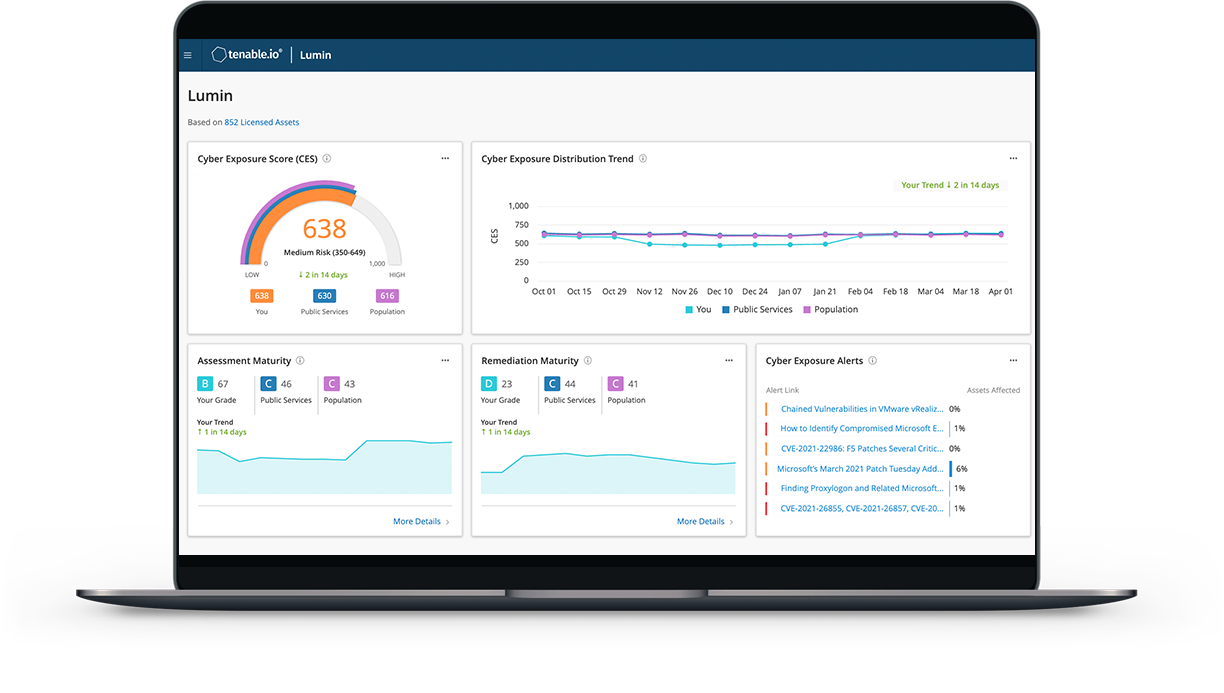
Advanced analysis and risk-based exposure scoring weighs asset value and criticality, vulnerabilities, threat context and security program effectiveness providing clear guidance about what to focus on.
Visualizations of the entire attack surface allow anyone from analyst to executive – to quickly understand and communicate your organization’s Cyber Exposure.
Exposure quantification and benchmarking allow you to compare your effectiveness for internal operations and against peers. Identify areas of focus and optimise security investments.
02 Vulnerability Management
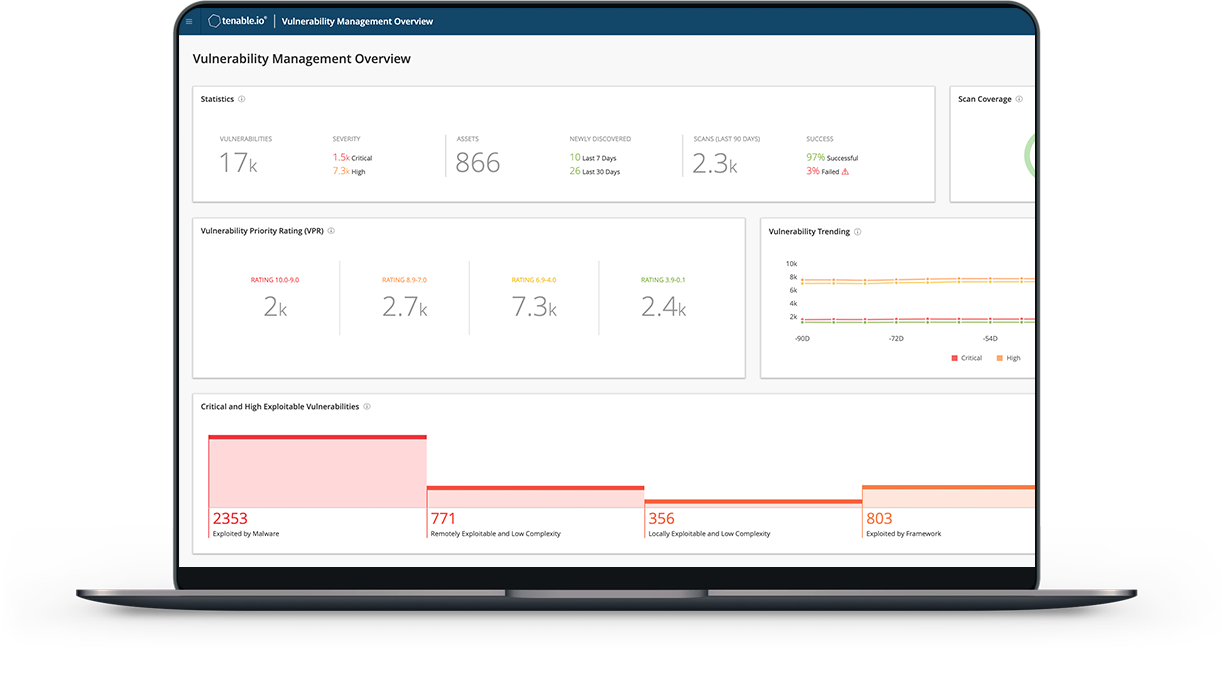
See Everything. Predict What Matters.
Understand your risk and know which vulnerabilities to fix first with Tenable.io
Get cloud-based vulnerability management for complete visibility into the assets and vulnerabilities in your organization.
Managed in the cloud and powered by Nessus technology, Tenable.io provides the industry's most comprehensive vulnerability coverage with the ability to predict which security issues to remediate first. It’s your complete end-to-end vulnerability management solution.
Struggling to Secure Your AWS Assets?
Try Frictionless Assessment
Say goodbye to network scanners and agents for the cloud. Frictionless Assessment in Tenable.io uses cloud-native tools to deliver continuous and near real-time visibility into your AWS exposures.
No scanners or agents to deploy. No scan schedules to configure. No software or credentials to manage. No more blind spots.
Setup takes seconds with actionable results in minutes. It’s completely frictionless.
Reduce Risk Across OT Operations, From Anywhere
If you are involved in industrial operations or critical infrastructure, you know risk does not stop with IT.
Tenable.ot now integrates with Tenable.io so you can gain full visibility of your OT risk and manage your environment from the cloud.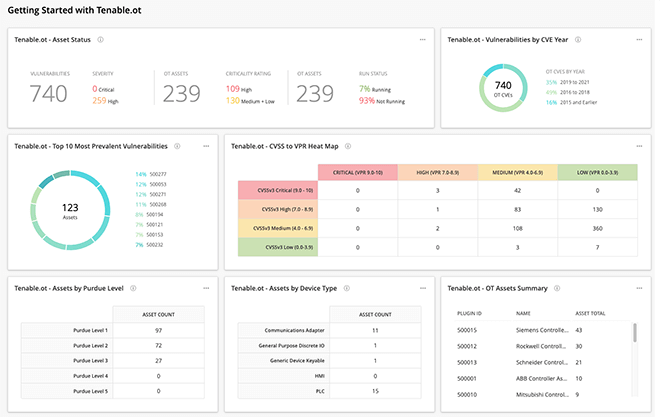
Active scanning, agents, passive monitoring, cloud connectors, external attack surface management and CMDB integrations provide unified visibility and a continuous view of all of your assets both known and previously unknown.
With coverage for more than 72K vulnerabilities, Tenable has the industry’s most extensive CVE and security configuration support to help you understand all of your exposures.
Combine vulnerability data, threat intelligence and data science for easy-to-understand risk scores to quickly assess risk and know which vulnerabilities to fix first.
03 Web App Security
Simple, scalable and automated vulnerability scanning for web applications
Create new scans in seconds and get actionable results in minutes with Tenable.io Web App Scanning
Take advantage of web application security built by the largest vulnerability research team in the industry.
From OWASP Top 10 risks to vulnerable web app components, Tenable.io Web App Scanning provides comprehensive and accurate vulnerability scanning. Gain full visibility of IT, cloud and web application vulnerabilities in a single platform.
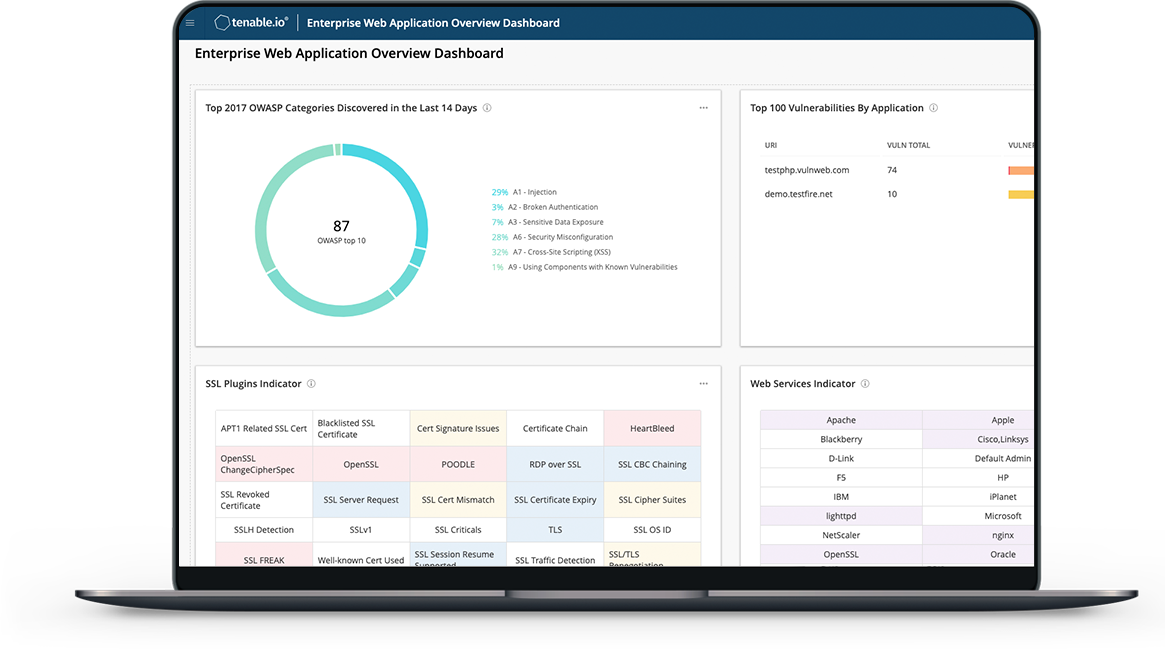
Chaallenges For Web Application Scanning
- Only a subset of web applications are assessed for vulnerabilities
- Many security teams lack application security specialists
- Web application scans yield an overwhelming number of web application vulnerabilities
The Tenable.io Solution
Tenable.io Web App Scanning provides easy-to-use, comprehensive and automated vulnerability scanning for modern web applications. Tenable.io WAS allows you to quickly configure and manage web app scans in a matter of minutes with minimal tuning.
Set up new web app scans in seconds by using the same workflows you are already familiar with. No need to spend hours or days manually tuning scans.
View vulnerable web app components and custom code vulnerabilities alongside your IT and cloud assets. Eliminate complexity from managing multiple, siloed solutions.
Comprehensive web app assessments built by experts give you confidence that your development teams aren’t wasting time on false positives or missing high-risk vulnerabilities.
04 Cloud Security
Unified Cloud Security Posture And Vulnerability Management
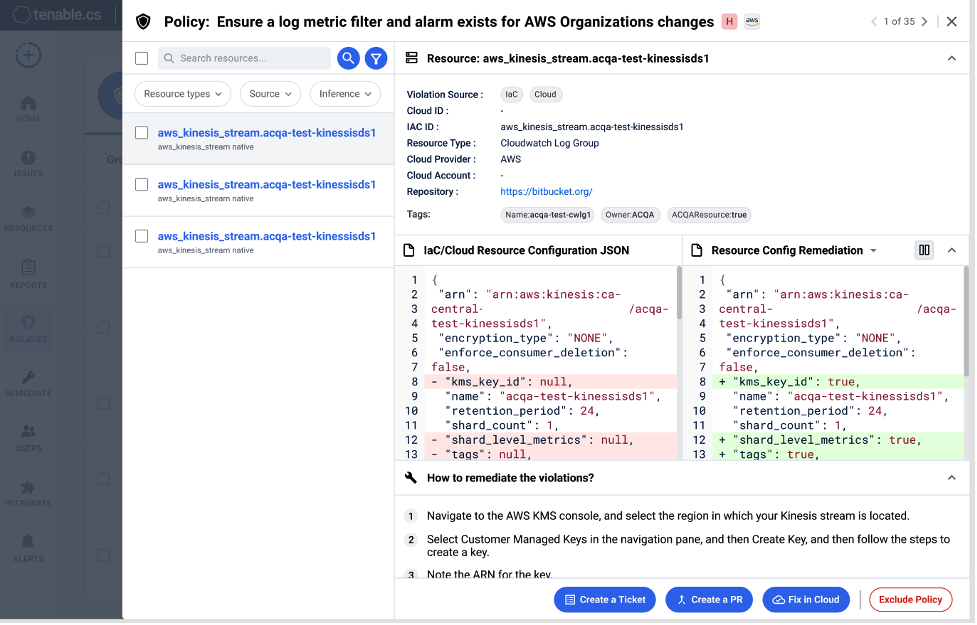
Take control of your cloud security program with Tenable.cs low-impact cloud agentless scanning, automated threat detection and risk prioritisation
Reduce your cloud security risks with Tenable. Developed by the leader in vulnerability management, Tenable.cs enables security teams to continuously assess the security posture of their cloud environments by maintaining a current inventory of cloud assets for proactive analysis whenever a new vulnerability is published without a user having to take any actions.
Accelerate Cloud Adoption Without Sacrificing Security Standards With Tenable Cloud Security
Wherever you are in your cloud journey, Tenable can help. We’ve been helping thousands of customers manage cloud vulnerabilities for years. We can help you architect a cloud security program that enables your dev teams to go fast and your security teams to maintain security and compliance standards.
Complete Cloud Visibility and Zero Day Threat Detection
Tenable.cs Agentless Assessment and Live Results enable security teams to quickly and easily discover and assess all their cloud assets. Data is continuously updated via live scans that are automatically triggered by any logged change event. Collected data is then integrated into the Tenable Research Vulnerability & Threat Library.
When a new vulnerability is published to the threat library, Live Results allows security teams to see if a vulnerability exists in their current asset inventory, without needing to execute a new scan.
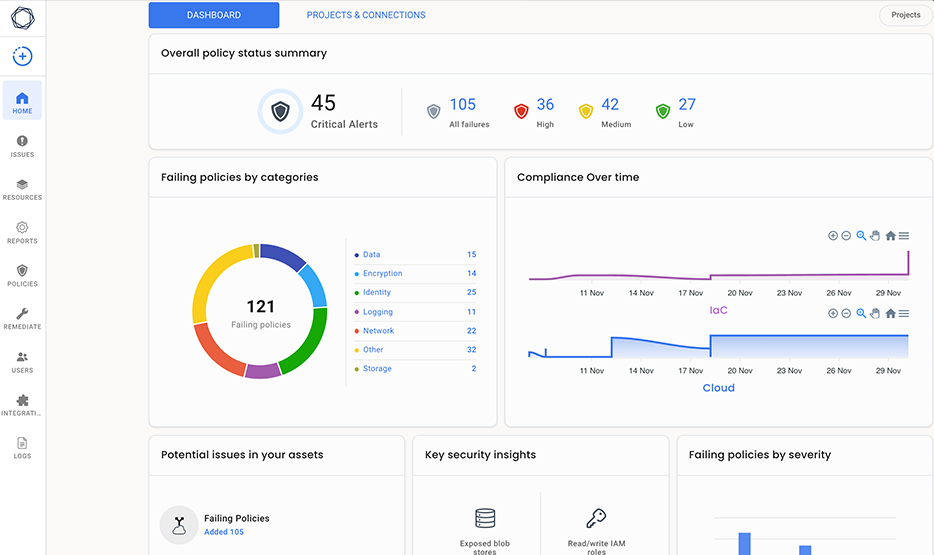
Cloud Security Posture Management (CSPM) and Governance
Tenable.cs provides cloud security teams the tools they need to apply, monitor and report on security and compliance policies across multi-cloud environments. Users can easily view information on non-compliance, misconfigurations, and even stop “high-risk” deployments from being made. Prioritised risks can be immediately submitted for remediation using an automated workflow.
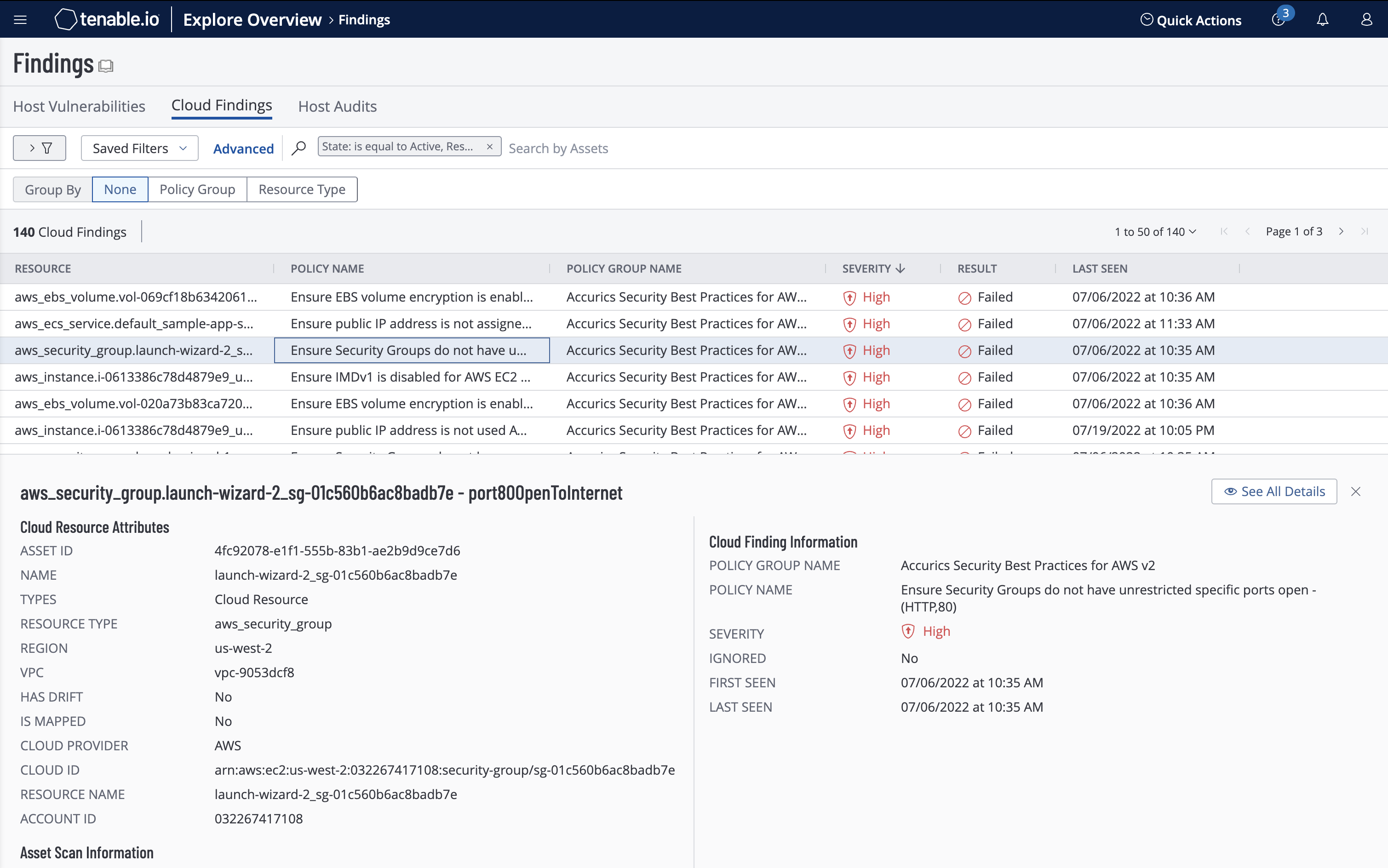
Shift-Left: Move from Remediation to Prevention with Dev-Friendly Tooling
Tenable.cs closes the divide between your security and DevOps teams by building upon Terrascan, one of the most popular open-source infrastructure as code (IaC) cloud security testing tools in the market. With Tenable.cs, you can reduce the number of runtime threats for remediation by shifting-left and addressing security weaknesses as part of the dev process.
Tenable 360 Approach To Cloud Security
New deployments to the cloud and published vulnerabilities never stop and neither can your organization’s cloud security program. When a new asset is deployed to the cloud we scan it. When a new vulnerability is published, we analyze the current inventory data to see if your cloud estate has it. By doing this, we help security teams take proactive control of their cloud environments without worrying about when their last scan was and if they may be at risk every time a new vulnerability is published.
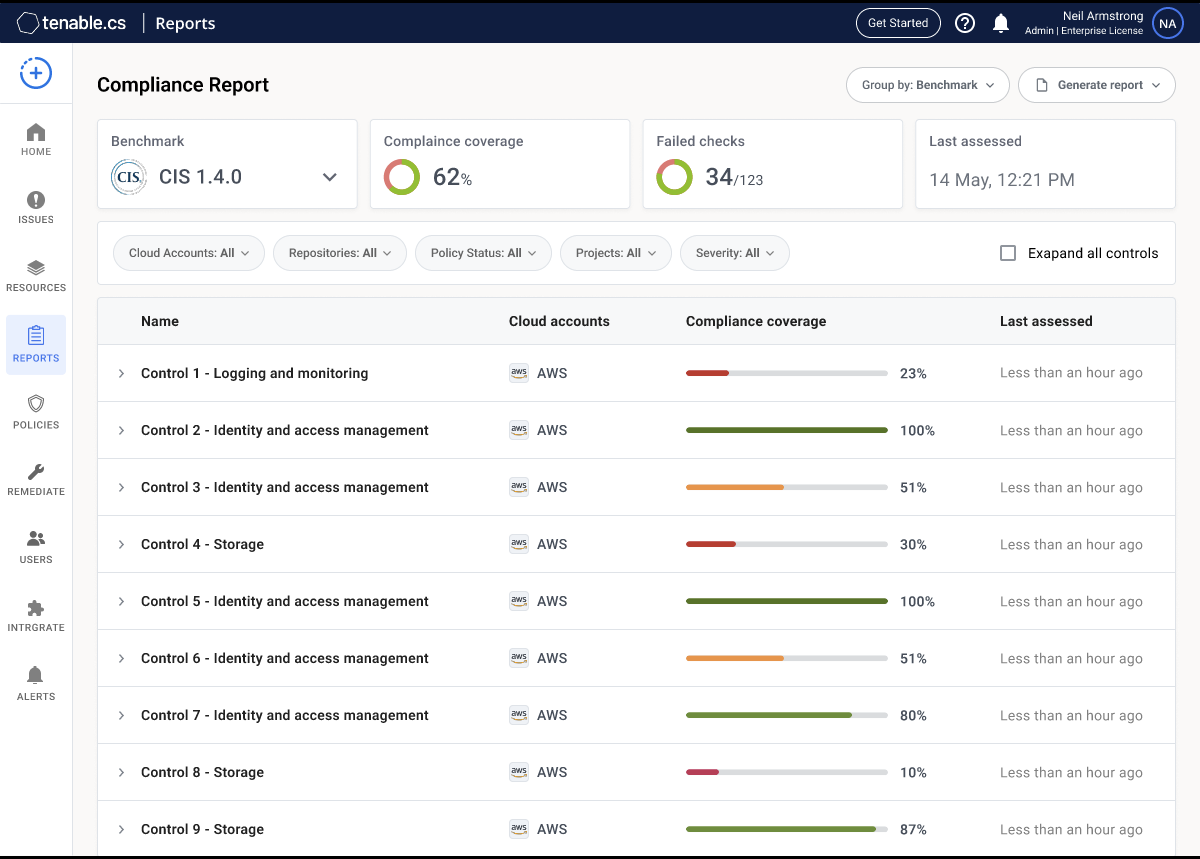
Drive Your Cloud Security Program With A Single Policy Framework
Automated policies are a core component to any enterprise class CSPM solution. Tenable.cs includes 1,400+ policies across 20+ standards such as CIS Benchmarks, SOC 2, PCI DSS, HIPAA, NYDFS and GDPR so you can enable policy guardrails across your entire organization in minutes. You can also quickly and easily define custom policies based on your individual needs.
05 Identity Security

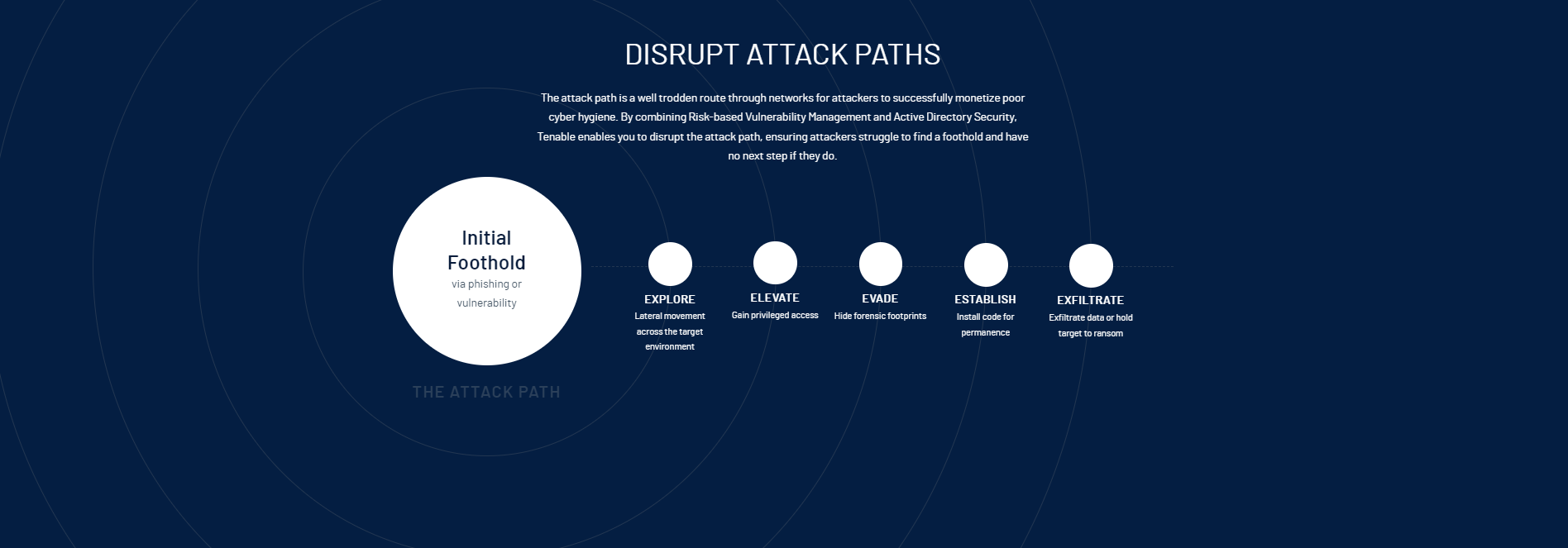
Secure Active Directory And Disrupt Attack Paths
Behind every breach headline is an insecure Active Directory (AD) deployment. AD has become the favored target for attackers to elevate privileges and facilitate lateral movement through leveraging known flaws and misconfigurations.
Unfortunately, most organisations struggle with Active Directory security due to misconfigurations piling up as domains increase in complexity, leaving security teams unable to find and fix flaws before they become business-impacting issues.
Tenable.ad enables you to see everything, predict what matters, and act to address risk in Active Directory to disrupt attack paths before attackers exploit them.
Find and Fix Active Directory Weaknesses Before Attacks Happen
Discover and prioritize weaknesses within your existing Active Directory domains and reduce your exposure by following Tenable.ad’s step-by-step remediation guidance.
Detect and Respond to Active Directory Attacks in Real Time
Detect Active Directory attacks like DCShadow, Brute Force, Password Spraying, DCSync and more. Tenable.ad enriches your SIEM, SOC or SOAR with attack insights so you can quickly respond and stop attacks.
Secure Active Directory
✅ Discover the underlying issues affecting your Active Directory
✅ Identify dangerous trust relationships Catch every change in your AD
✅ Make the link between AD changes and malicious actions
✅ Analyze in-depth details of attacks
✅ Explore MITRE ATT&CK descriptions directly from incident details
Continuously Detect And Prevent Active Directory Attacks
Prevents and detects sophisticated Active Directory attacks without agents and privileges.
Check the security of Azure Active Directory Domain Services, AWS Directory Service, or Google Managed Service for Active Directory in real time.
Tenable.ad provides the flexibility of two architectural designs. On-prem to keep your data on-site and under your control. SaaS, so you can leverage the cloud.
06 Attack Surface Management

Gain Visibility Into Your External Attack Surface
Visibility is foundational to cybersecurity, yet few organisations have mastered it. As more assets, services and applications reside on the internet, security teams are unaware of their full digital footprint. The reality is that people on the outside often know more about the organisation’s attack surface than those within.
Tenable.asm is the industry’s first external attack surface management (EASM) solution fully integrated into a vulnerability management platform. Tenable.asm continuously maps the entire internet and discovers connections to your internet-facing assets so that you can assess the security posture of your entire external attack surface.
Your EXTERNAL ATTACK SURFACE poses one of the highest risks and is now the easiest to understand with Tenable.asm
62% of an organisation’s attack surface is estimated to be known to cybersecurity today
73% of organisations are worried about their growing attack surface
62% of organisations have blind spots that hamper security efforts
Discover What You Own
Discovery is key. Find more with Tenable.asm to access an attack surface map of more than 5 billion assets to discover domains related to assets in your inventory. Get more done with notifications on changes in your attack surface for continuous monitoring.
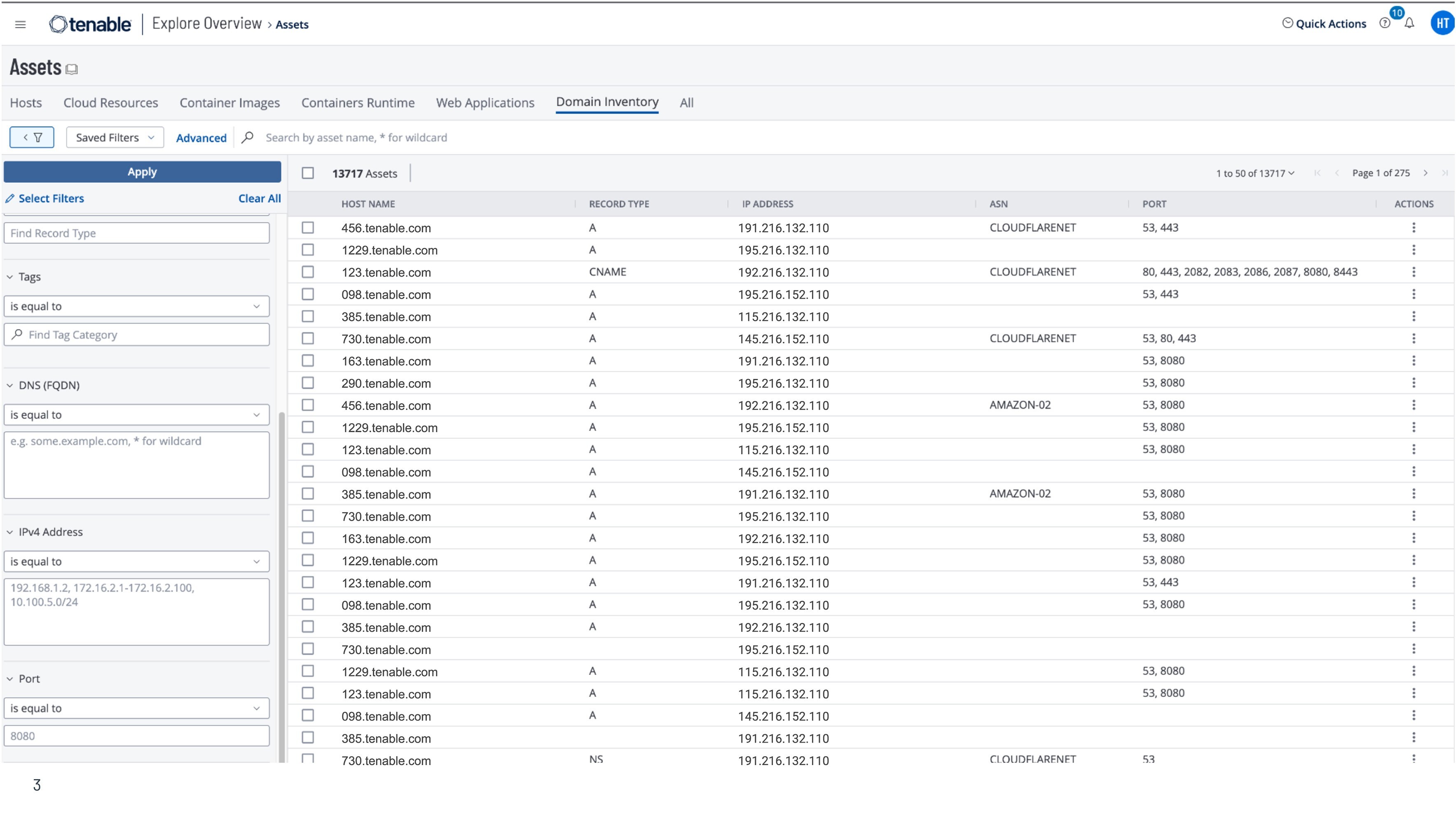
Understand Business Context
Get full business context by leveraging more than 200 fields of metadata to help you make more informed decisions about previously unknown internet-connected assets. Streamline asset management by leveraging filters, tags and datatypes to understand your full external footprint.
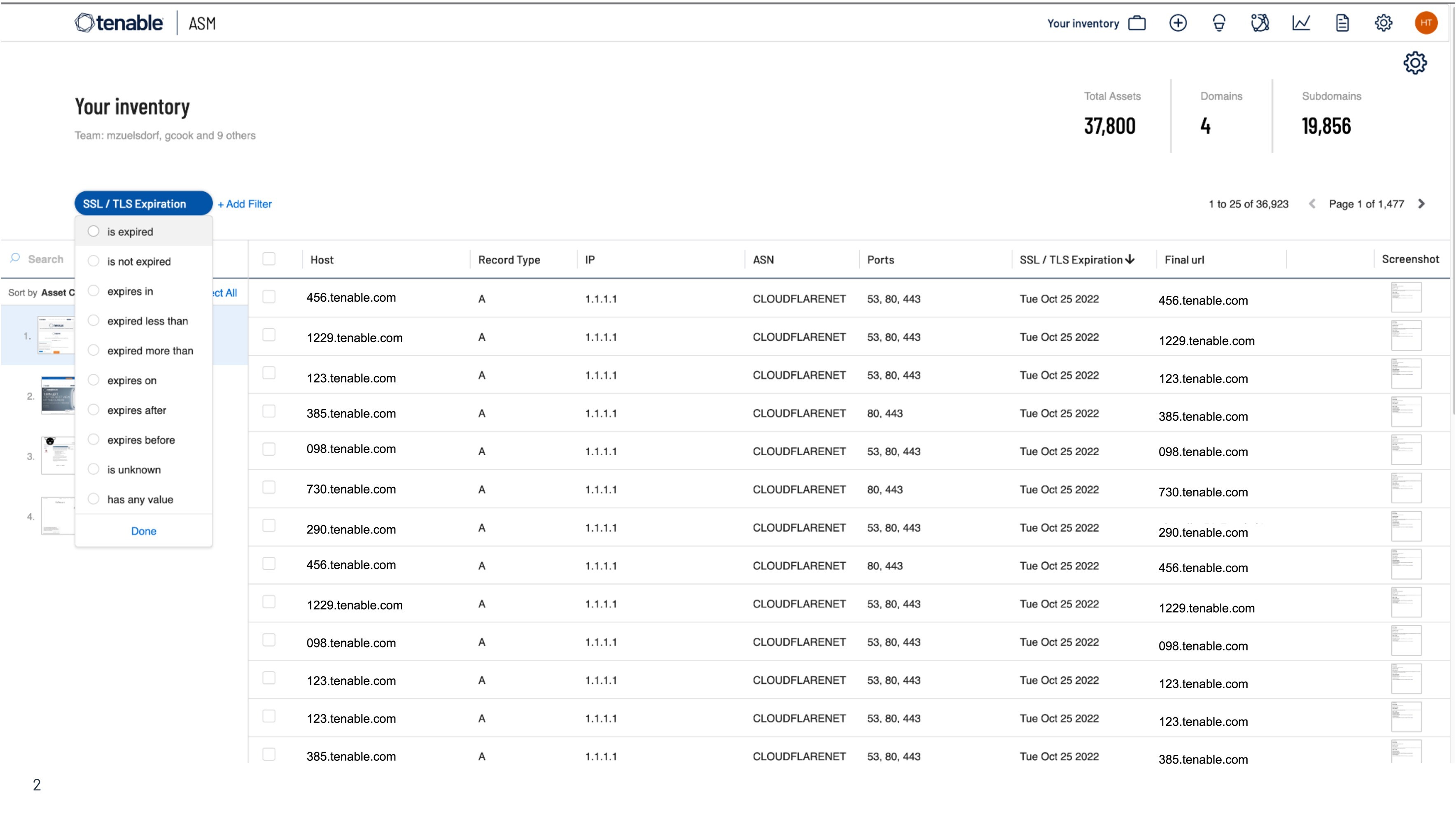
Easily Assess for Cyber Risk
Your external attack surface assets and exposure data is fully integrated into Tenable One, Tenable.io, Tenable.sc. Seamlessly kick-off new scans of unassessed assets to scan for blind spots and comprehensive coverage across your external attack surface. Want more? Tenable.asm is available as an add on.
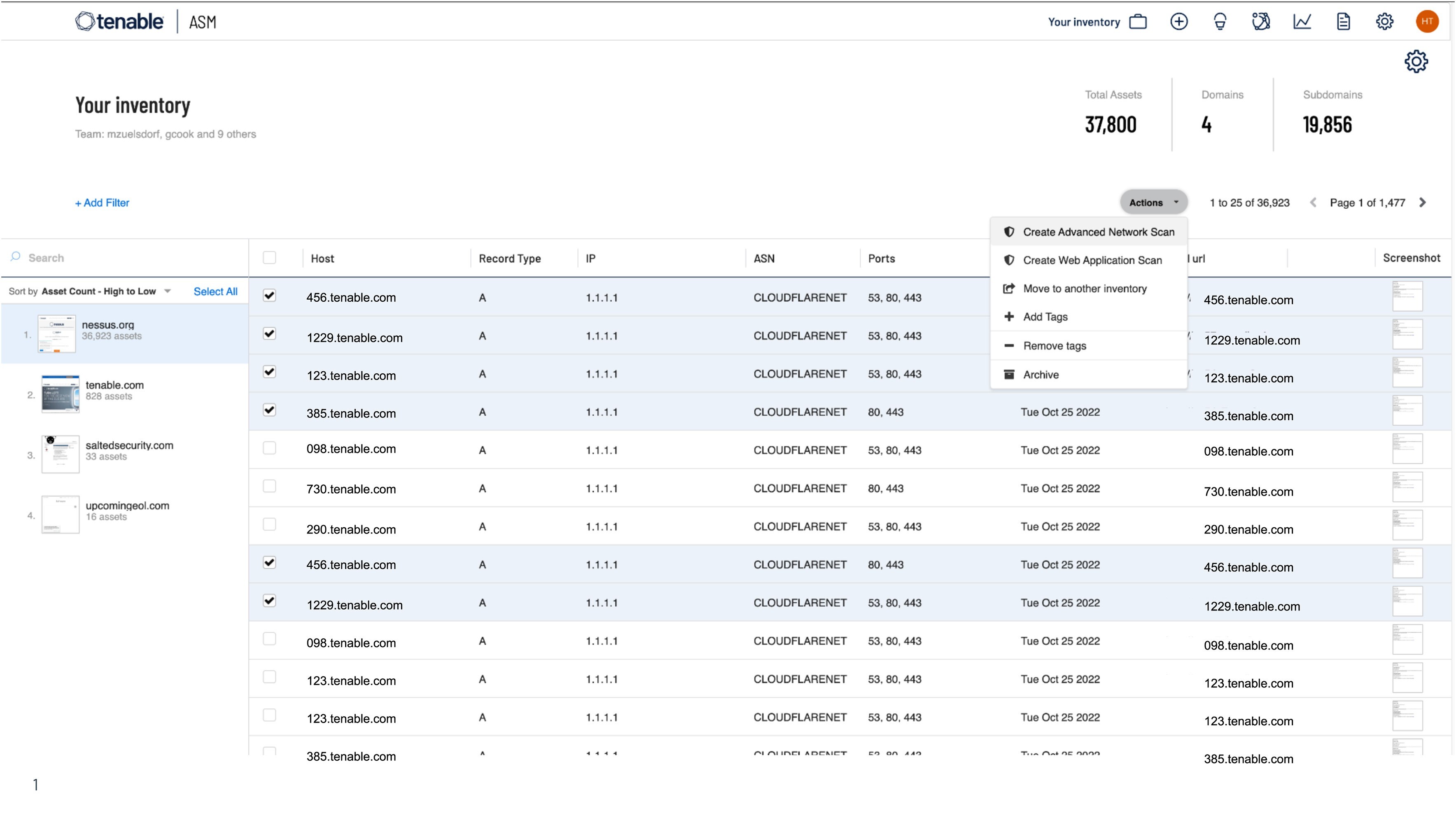
Mitigate risk and avert potential threats by knowing exactly what you own. Establishing the attack surface is foundational to security strategy.
Reveal locations where personally identifiable information (PII) is captured and stored, to fully comply with industry regulations.
Secure your brand by recognizing expired marketing campaigns, misspellings, SEO opportunities, and misuse.
Discern risk early. Instantly see every internet-facing asset of your target company before acquisition.
Reveal the attack surface of current and potential competitors to identify strategic opportunities.
Understand which assets have non-compliant technology, missing legal disclaimers and expired copyright notices.
Copyright © 2025 All Rights Reserved by SolutionsPT.



